TechStunnel: Difference between revisions
From Redrock Wiki
No edit summary |
No edit summary |
||
| (6 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
{{40EOL}} | |||
{| style="width:100%; vertical-align:top; " | {| style="width:100%; vertical-align:top; " | ||
| style="width:250px; vertical-align:top; padding:2px 15px 2px 2px;" | {{TechDocsTOC}} | | style="width:250px; vertical-align:top; padding:2px 15px 2px 2px;" | {{TechDocsTOC}} | ||
| Line 4: | Line 5: | ||
{| style="width:100%; vertical-align:top; " | {| style="width:100%; vertical-align:top; " | ||
<span style="vertical-align:top; font-size:160%; color:#7c1911;"><big>HTTPS Connections to your Trac System</big></span><HR> | |||
The Trac System doesn't inherently support secure connections over HTTPS, a proxy such as Stunnel must be used to facilitate this instead. Other proxies may be used, but Stunnel is the only option that Redrock Software can offer support for. If your Trac System is hosted by Redrock, you will already be able to connect over HTTPS using our domain name (example.go-redrock.com). If you would like to use a custom domain for your hosted system, create a CNAME record pointing to <span style="color:red">rscprxy.go-redrock.com</span> and provide an Apache X509-compatible certificate and key to us. The cert and key can be uploaded to our SFTP server (same location as your import files). We are unable to provide CSR/.req files. For non-hosted instances, continue reading. | |||
<hr> | |||
<big><span style="color:#7c1911">Stunnel / Proxies</big></span><br> | |||
There are several options for implementing HTTPS for your Trac server. A web server for HTTPS proxying such as Apache or Nginx can be used, or you can utilize a dedicated proxying application such as HAProxy. These could be running on the same or a separate server. Only internal traffic between the proxy and the Trac System would be in plaintext. As an alternative, a 3rd party application (like Stunnel) may be installed on your Trac System server. The latter is what we at Redrock are able to offically support. | |||
Stunnel is a program that encrypts all connections to your server. Stunnel facilitates this by acting as a proxy between users' browsers and the Trac application. A user would open a web browser and enter in your server address, e.g., '''<nowiki>https://trac.example.edu/</nowiki>'''. Stunnel receives the encrypted request, decrypts the request, and then forwards the request to the Trac application. The Trac application will then issue a response back to Stunnel, Stunnel encrypts the response, and then forwards the encrypted response back to the user's browser. With this method, all network traffic from the server to the client is encrypted while the Trac application communicates with Stunnel locally in an unencrypted format. | |||
<hr> | |||
<big><span style="color:#7c1911">Installing Stunnel</big></span><br> | |||
Click [https://www.stunnel.org/downloads.html on this link] to download and install the latest stable win64-installer. Once the .exe file has downloaded, install Stunnel using the default options. If you already have a certificate, you can close the prompt to generate a certificate/CSR that appears during installation. | |||
<hr> | |||
<big><span style="color:#7c1911">Certificate Format</big></span><br> | |||
The necessary SSL files are a certificate (typically cert.pem) and a key file (typically key.pem). You will need to obtain your own Apache X509-compatible certificate from any trusted Certificate Authority. Some CAs will provide you with a chained certificate, which we will have to combine in order to make the file compatible. Place the certificate and key files in your Stunnel config directory (C:\Program Files (x86)\stunnel\config). Keep a copy of your req.pem (CSR) file to request your new certificate when it expires. | |||
In the event that you only have a .pfx file available, it can be split into separate certificate and key files for use in Stunnel with the following OpenSSL commands. | |||
<syntaxhighlight style="border: 1px dashed black" lang="bash"> | |||
openssl pkcs12 -in input.pfx -clcerts -nokeys -out output.crt | |||
openssl pkcs12 -nocerts -in input.pfx -out output.key -nodes | |||
</syntaxhighlight> | |||
<hr> | |||
<big><span style="color:#7c1911">Stunnel Config File</big></span><br> | |||
The Stunnel configuration file (stunnel.conf) is located in the C:\Program Files (x86)\stunnel\config directory by default and must be edited. Below is a good default config file. Simply replace the contents of stunnel.conf with this, replacing the IP address and cert/key file names as needed.<br /><br /> | |||
'''Sample stunnel configuration file by Redrock Software'''<br /> | '''Sample stunnel configuration file by Redrock Software'''<br /> | ||
<syntaxhighlight style="max-width:60em; border: 1px dashed black" lang="ini"> | |||
; identify the private key and public certificate files | ; identify the private key and public certificate files, placed in the config directory | ||
cert = cert.pem | cert = cert.pem | ||
key = key.pem | key = key.pem | ||
| Line 61: | Line 46: | ||
socket = l:TCP_NODELAY=1 | socket = l:TCP_NODELAY=1 | ||
socket = r:TCP_NODELAY=1 | socket = r:TCP_NODELAY=1 | ||
; Service-level configuration | ; Service-level configuration | ||
[https] | [https] | ||
accept = 443 | accept = 192.168.0.42:443 | ||
connect = 192.168.0. | connect = 192.168.0.42:81 | ||
TIMEOUTclose = 0 | TIMEOUTclose = 0 | ||
; Force TLS 1.2 | |||
options = NO_SSLv2 | |||
options = NO_SSLv3 | |||
sslVersionMin = TLSv1.2 | |||
; Ciphers (optional) | |||
ciphers = ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-DSS-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384:ECDH-RSA-AES256-GCM-SHA384:ECDH-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:DHE-RSA-AES128-GCM-SHA256:ECDH-RSA-AES128-GCM-SHA256:ECDH-ECDSA-AES128-GCM-SHA256 | |||
</syntaxhighlight> | |||
<!----------- Prefs.ini ------------> | |||
<hr> | |||
<big><span style="color:#7c1911">Trac System Prefs.ini File</big></span><br> | |||
After installing Stunnel, go to your Trac installation folder, and edit /database/prefs.ini. Edit the following lines depending on your configuration, the Trac System must be restarted to apply changed. | |||
If your installation is not using Stunnel and is only accessible via HTTP. | |||
<syntaxhighlight style="border: 1px dashed black" lang="ini"> | |||
[Server] | |||
serverPort=80 | |||
serverPort2= | |||
serverProcs=15 | |||
serverProcs2=0 | |||
redirect=None | |||
redirect2=None | |||
</syntaxhighlight> | |||
If your installation is using Stunnel and will be accessible via HTTPS. | |||
<syntaxhighlight style="border: 1px dashed black" lang="ini"> | |||
[Server] | |||
serverPort=80 | |||
serverPort2=81 | |||
serverProcs=5 | |||
serverProcs2=15 | |||
redirect=https://your.trac.domain.edu | |||
redirect2=None | |||
</syntaxhighlight><br> | |||
The | The 'serverPort' variables determine what ports your Trac System is accessible at. The purpose of the second port is for proxies like Stunnel, as incoming connections on port 80 can be redirected to 443 and Stunnel can communicate locally with Trac over port 81 (or any other preferred port).<br><br> | ||
The 'serverProcs' variables are effectively the processing resources available on each port. The sum total of these two variables should not exceed 20. If your Trac System is only available on port 80, then serverProcs can be set to 15 and serverProcs2 can be 0 (unused). If Stunnel is used, the only purpose of port 80 will be to redirect users to 443 (81 internally). In this case, serverProcs2 should be set to 15 and serverProcs doesn't need as much as it will only be redirecting users.<br><br> | |||
The 'redirect' variables determine where users are sent when they reach the Trac System on each port. If your Trac System is only accessible on port 80, both redirect variables can be left as "None" as there's nowhere to redirect to. If Stunnel is used, redirect (not redirect2) should send users to your Trac System's https:// URL.<br><br> | |||
'ServerSecure' and 'ServerSecure2' should both be kept at the default value of 'None' in either case. | |||
<!----------- Stunnel Service ------------> | |||
<hr> | |||
<big><span style="color:#7c1911">Configure Stunnel as a Service</big></span><br> | |||
To install Stunnel as a service, run the following command in a Command Prompt window. Note that the Stunnel service and Stunnel application (started from the /bin folder) cannot run at the same time and will cause errors. Always stop the Stunnel application before starting the service, and vice versa. | |||
<syntaxhighlight style="border: 1px dashed black" lang="text"> | |||
stunnel.exe -install | |||
</syntaxhighlight> | |||
__NOTOC__ | __NOTOC__ | ||
[[Category:Trac 4]] | |||
Latest revision as of 11:19, 26 March 2024
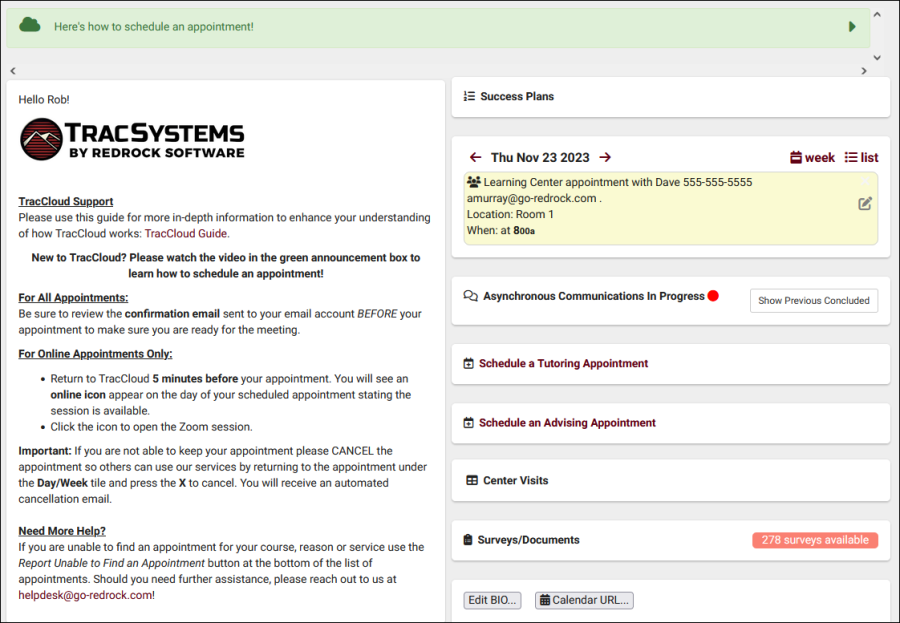
The legacy Trac 4.0 version of TutorTrac/AdvisorTrac/FitnessTrac is no longer receiving updates and will be end-of-life in 2025. Click here to schedule a TracCloud demo or reach out to sales@go-redrock.com for migration pricing or contract details.
New, easy to use interface
TracCloud features a modern, easy to use, and mobile-friendly interface, allowing you to easily find and manage your data as you need. Students, staff, and faculty will have a much easier time navigating through the system and accessing the data they need. The new dashboard offers many easy to access widgets to view and manage your data.
New Features
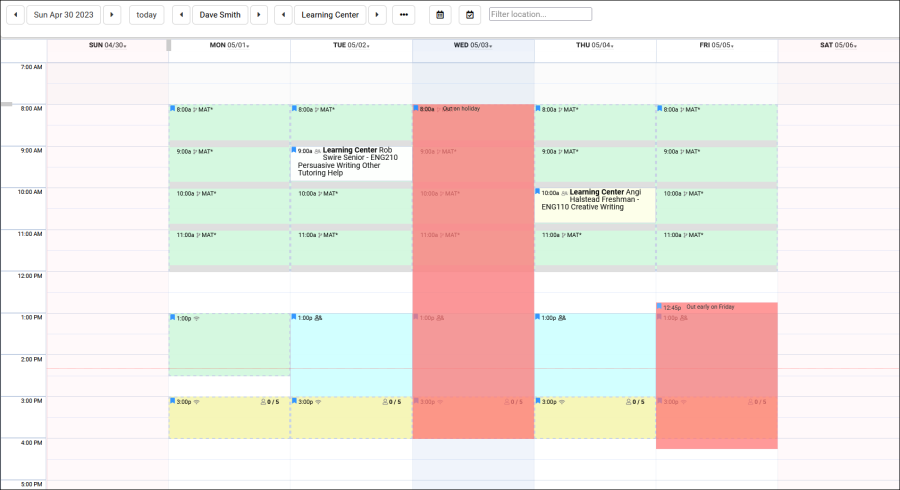
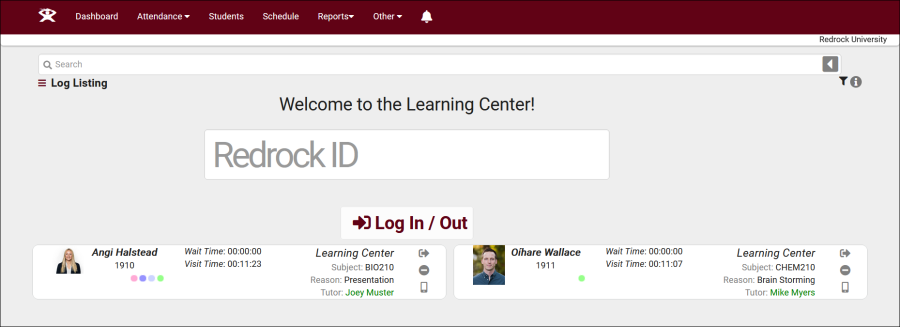
Export almost any report into Excel. Static and dynamic QR codes for touchless-kiosk environments. Unlimited custom data fields in student records, visits, appointments, and more. Customizable views of listing pages. Student timelines. Twig and HTML-supported emails and system messages. Customizable log listing and kiosk views. Center descriptions. New reports. Student success plans as a new module, along with work plans for staff. The full list of changes couldn't fit in this article, and more is being added all the time. Relating to the schedule specifically, you'll find a new appointments listing, availability badges, custom search appointment links and QR codes, unlimited customizable max appointment rules, asynchronous appointment support, and more.
Customizable
With Twig support, you can personalize system messages, upcoming appointment lists, emails, and more based on the users who are viewing/receiving them. From simple changes like greeting the user by name to completely changing an email based on if the related appointment was in-person or online, in a certain center, for a certain reason, even if a certain custom field in the student's profile has a specific value. This extends to the log listing and kiosks as well, where you can add or remove fields, rearrange the data that's displayed, and add custom formatting with HTML and Twig.
Faster
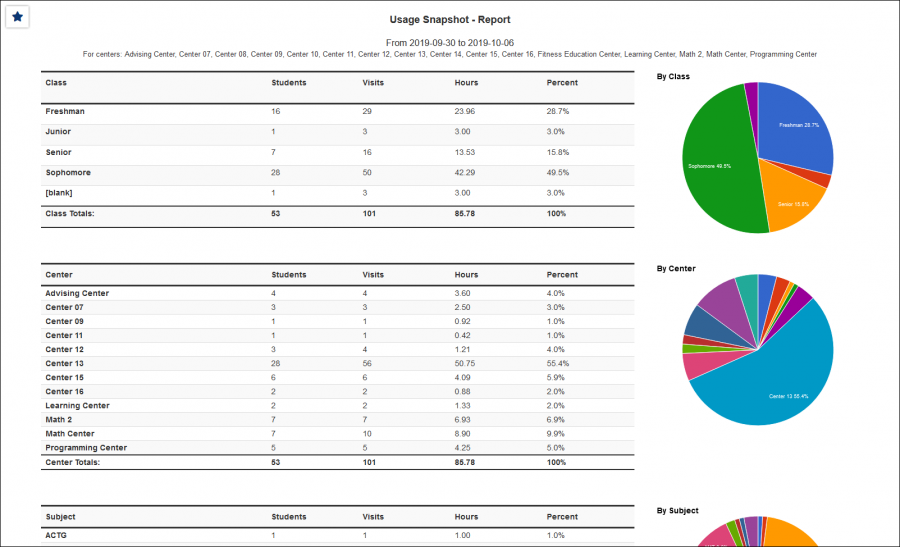
Rewritten from the ground up hosted on AWS, using a MySQL database, TracCloud is faster in every way. This performance increase compared to Trac 4.0 can be noticed throughout the entire system, with reports being especially improved. Even the biggest reports in TracCloud load within a few seconds.
Migrate Existing Data
Migrate your existing data from Trac 4.0, allowing you to pick up right where you left off. We'll work with you to plan out your migration, coordinating with your IT, and training your system administrators to get you started in TracCloud.
|
HTTPS Connections to your Trac System The Trac System doesn't inherently support secure connections over HTTPS, a proxy such as Stunnel must be used to facilitate this instead. Other proxies may be used, but Stunnel is the only option that Redrock Software can offer support for. If your Trac System is hosted by Redrock, you will already be able to connect over HTTPS using our domain name (example.go-redrock.com). If you would like to use a custom domain for your hosted system, create a CNAME record pointing to rscprxy.go-redrock.com and provide an Apache X509-compatible certificate and key to us. The cert and key can be uploaded to our SFTP server (same location as your import files). We are unable to provide CSR/.req files. For non-hosted instances, continue reading. Stunnel / Proxies There are several options for implementing HTTPS for your Trac server. A web server for HTTPS proxying such as Apache or Nginx can be used, or you can utilize a dedicated proxying application such as HAProxy. These could be running on the same or a separate server. Only internal traffic between the proxy and the Trac System would be in plaintext. As an alternative, a 3rd party application (like Stunnel) may be installed on your Trac System server. The latter is what we at Redrock are able to offically support. Stunnel is a program that encrypts all connections to your server. Stunnel facilitates this by acting as a proxy between users' browsers and the Trac application. A user would open a web browser and enter in your server address, e.g., https://trac.example.edu/. Stunnel receives the encrypted request, decrypts the request, and then forwards the request to the Trac application. The Trac application will then issue a response back to Stunnel, Stunnel encrypts the response, and then forwards the encrypted response back to the user's browser. With this method, all network traffic from the server to the client is encrypted while the Trac application communicates with Stunnel locally in an unencrypted format. Installing Stunnel Click on this link to download and install the latest stable win64-installer. Once the .exe file has downloaded, install Stunnel using the default options. If you already have a certificate, you can close the prompt to generate a certificate/CSR that appears during installation. Certificate Format The necessary SSL files are a certificate (typically cert.pem) and a key file (typically key.pem). You will need to obtain your own Apache X509-compatible certificate from any trusted Certificate Authority. Some CAs will provide you with a chained certificate, which we will have to combine in order to make the file compatible. Place the certificate and key files in your Stunnel config directory (C:\Program Files (x86)\stunnel\config). Keep a copy of your req.pem (CSR) file to request your new certificate when it expires. In the event that you only have a .pfx file available, it can be split into separate certificate and key files for use in Stunnel with the following OpenSSL commands. openssl pkcs12 -in input.pfx -clcerts -nokeys -out output.crt
openssl pkcs12 -nocerts -in input.pfx -out output.key -nodes
Stunnel Config File The Stunnel configuration file (stunnel.conf) is located in the C:\Program Files (x86)\stunnel\config directory by default and must be edited. Below is a good default config file. Simply replace the contents of stunnel.conf with this, replacing the IP address and cert/key file names as needed. Sample stunnel configuration file by Redrock Software ; identify the private key and public certificate files, placed in the config directory
cert = cert.pem
key = key.pem
; Some performance tunings
socket = l:TCP_NODELAY=1
socket = r:TCP_NODELAY=1
; Service-level configuration
[https]
accept = 192.168.0.42:443
connect = 192.168.0.42:81
TIMEOUTclose = 0
; Force TLS 1.2
options = NO_SSLv2
options = NO_SSLv3
sslVersionMin = TLSv1.2
; Ciphers (optional)
ciphers = ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-DSS-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384:ECDH-RSA-AES256-GCM-SHA384:ECDH-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:DHE-RSA-AES128-GCM-SHA256:ECDH-RSA-AES128-GCM-SHA256:ECDH-ECDSA-AES128-GCM-SHA256
Trac System Prefs.ini File After installing Stunnel, go to your Trac installation folder, and edit /database/prefs.ini. Edit the following lines depending on your configuration, the Trac System must be restarted to apply changed. If your installation is not using Stunnel and is only accessible via HTTP. [Server]
serverPort=80
serverPort2=
serverProcs=15
serverProcs2=0
redirect=None
redirect2=None
If your installation is using Stunnel and will be accessible via HTTPS. [Server]
serverPort=80
serverPort2=81
serverProcs=5
serverProcs2=15
redirect=https://your.trac.domain.edu
redirect2=None
The 'serverPort' variables determine what ports your Trac System is accessible at. The purpose of the second port is for proxies like Stunnel, as incoming connections on port 80 can be redirected to 443 and Stunnel can communicate locally with Trac over port 81 (or any other preferred port). The 'serverProcs' variables are effectively the processing resources available on each port. The sum total of these two variables should not exceed 20. If your Trac System is only available on port 80, then serverProcs can be set to 15 and serverProcs2 can be 0 (unused). If Stunnel is used, the only purpose of port 80 will be to redirect users to 443 (81 internally). In this case, serverProcs2 should be set to 15 and serverProcs doesn't need as much as it will only be redirecting users. The 'redirect' variables determine where users are sent when they reach the Trac System on each port. If your Trac System is only accessible on port 80, both redirect variables can be left as "None" as there's nowhere to redirect to. If Stunnel is used, redirect (not redirect2) should send users to your Trac System's https:// URL. 'ServerSecure' and 'ServerSecure2' should both be kept at the default value of 'None' in either case. Configure Stunnel as a Service To install Stunnel as a service, run the following command in a Command Prompt window. Note that the Stunnel service and Stunnel application (started from the /bin folder) cannot run at the same time and will cause errors. Always stop the Stunnel application before starting the service, and vice versa. stunnel.exe -install
|