TracCloud: Single Sign-On: Difference between revisions
From Redrock Wiki
No edit summary |
m (Redrock moved page TracCloud: Single Sign-On to TracCloud: Single Sign-On) |
||
| (16 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
{ | {{TracCloudGuideTabs}} | ||
<div class="tcWidgetPage"> | |||
<div class="category"> | |||
{{TracCloudTechTOC}} | |||
</div> | |||
<big><b>TracCloud Single Sign-on Configuration</b></big><br> | <big><b>TracCloud Single Sign-on Configuration</b></big><br> | ||
| Line 8: | Line 9: | ||
We can be reached at [mailto:helpdesk@go-redrock.com helpdesk@go-redrock.com] | We can be reached at [mailto:helpdesk@go-redrock.com helpdesk@go-redrock.com] | ||
< | <div class="line"></div> | ||
'''With Redrock Software's Assistance''' | |||
<div class="line"></div> | |||
==SAML== | ==SAML== | ||
To setup SAML authentication, the following steps will need to be completed. At least one of the attributes being sent must match the contents of the username field in your Trac System, typically the first part of the email address. | To setup SAML authentication, the following steps will need to be completed. <span style="color:red">At least one of the attributes being sent must match the contents of the username field in your Trac System, typically the first part of the email address. We can also use ID number, full email address, or other unique identifiers, but handle/username is preferred.</span> Single logout (SLO) must be enabled for security purposes. | ||
<big>1. Install our Metadata</big> | <big>1. Install our Metadata</big> | ||
| Line 23: | Line 26: | ||
:This makes implementing SAML on your system significantly faster, but isn't required. | :This makes implementing SAML on your system significantly faster, but isn't required. | ||
<hr> | <hr> | ||
==CAS== | ==CAS== | ||
| Line 51: | Line 55: | ||
Multiple base DN searches can be performed if needed. | Multiple base DN searches can be performed if needed. | ||
<hr> | <hr> | ||
| | '''Without Redrock Software's Assistance''' | ||
If you're comfortable applying changes here and already have the information above, you can put these settings in place with any SysAdmin account. If you're having any trouble with these settings, feel free to reach out to us at [mailto:helpdesk@go-redrock.com helpdesk@go-redrock.com] or by [https://helpdesk.go-redrock.com submitting a helpdesk ticket]. LDAP currently requires additional configuration not available to non-Redrock accounts, reach out to us directly if you plan on using LDAP. | |||
<HR> | |||
<div style="float: left; margin-top: 0em; margin-bottom: 1em"><big>SAML Configuration</big></div><div class="mw-collapsible mw-collapsed"><br><br> | |||
<i>Other > Other Options > Preferences > Login & Security Settings > SAML</i> | |||
[[File:8589517.png|800px]] | |||
<big>1. Install our Metadata</big> | |||
::Redrock Metadata: https://sso.trac.cloud/simplesaml/module.php/saml/sp/metadata.php/trac5-saml<br><br> | |||
<big>2. Fill out SAML settings</big> | |||
:* <b>Trac Return URL</b> | |||
:::"<span style="color:red"><nowiki>https://traccloud.go-redrock.com/campuscode/trac/ajax.php?proc=sso_validate</nowiki></span>" | |||
:::Replace 'campus code' with your campus code, as seen in your URL. Otherwise static. Must be lowercase. | |||
::If using a custom URL, use that in place of traccloud.go-redrock.com/campuscode | |||
:* <b>SAML Relay URL</b> | |||
:::"<span style="color:red"><nowiki>https://saml2.go-redrock.com/relay.php</nowiki></span>" | |||
:::This is static and never changes. | |||
:* <b>Authentication Order</b> | |||
:::Your staff may have more than one account type in the Trac System. You can use the "Authentication Order" preference to determine which account type authenticates first. | |||
:* <b>Install your Metadata in the Primary Metadata field</b> | |||
:::[[File:2807471.png|500px]] | |||
:::After submitting, your Entity ID field will be populated automatically. If you require a duel-tenant configuration, reach out to us at [mailto:helpdesk@go-redrock.com helpdesk@go-redrock.com] for assistance.<br><br> | |||
<big>3. Retrieve your attributes</big> | |||
:[[File:6978515.png|500px]] | |||
:Navigate to the provided URL in a Private/Incognito browser and login, you will be provided with a list of attributes and their value for the account that you used. Find the attribute that works for your system (e.g., first part of email address) and copy the name of that attribute into the "Attribute containing unique ID" field in TracCloud. This will need to correspond to the Username fields of accounts in the system.<br><br> | |||
<big>4. Enable SAML</big> | |||
:Enable the toggle option in the top-right corner of your SAML window to enable SAML authentication for future logins. | |||
:[[File:75kj5yh56j56kj5ryh.png|800px]]<br><br> | |||
</div> | |||
<HR> | |||
<div style="float: left; margin-top: 0em; margin-bottom: 1em"><big>CAS Configuration</big></div><div class="mw-collapsible mw-collapsed"><br><br> | |||
<i>Other > Other Options > Preferences > Login & Security Settings > CAS</i> | |||
[[File:6231962.png|800px]] | |||
<br><br> | |||
<big>1. Add Redrock as an authorized service</big> | |||
:Here is our URL: https://sso.trac.cloud/cas_return.php | |||
<big>2. Fill out CAS settings</big> | |||
:* <b>CAS Relay URL</b> | |||
:::"<span style="color:red"><nowiki>https://sso.trac.cloud/relay.php</nowiki></span>" | |||
:::This value is static and should not be changed. | |||
:* <b>Ticket URL</b> | |||
:::Place your CAS Login URL here. | |||
:* <b>Ticket Param</b> | |||
:::Typically "<span style="color:red">ticket</span>" | |||
:*<b>Validate URL</b> | |||
:::Place your CAS Validate URL here. | |||
:*<b>CAS Version</b> | |||
:::Typically "<span style="color:red">2.0</span>" | |||
:*<b>User Name Attribute</b> | |||
:::Typically "<span style="color:red">cas:user</span>" | |||
:*<b>Trac Return URL</b> | |||
:::Place your CAS Logout URL here. | |||
:* <b>Deauth when visiting KIOSK</b> | |||
:::Kiosks are typically student-facing. If this is checked, it ends the SSO session to prevent a user from navigating to other campus services or even logging back into TracCloud. | |||
<big>3. Enable CAS</big> | |||
:Enable the toggle option in the top-right corner of your CAS window to enable CAS authentication for future logins. | |||
:[[File:J54yh545m56j5j.png|800px]] | |||
</div> | |||
<HR> | |||
<div style="float: left; margin-top: 0em; margin-bottom: 1em"><big>Additional Login/Logout Settings</big></div><div class="mw-collapsible mw-collapsed"><br><br> | |||
After setting up the SSO protocol, there are a few optional settings to configure, detailed below. | |||
[[File:1811987.png|800px]]<br><br> | |||
* <b>Log Off Redirect URL</b> | |||
::This is the URL that users will be taken to when logging out of the Trac System, typically used to redirect users to a page that ends their single sign-on session.<br><br> | |||
* <b>Custom "No Access" Page URL</b> | |||
::By default, if a user attempts to access a page that they don't have access to, a generic "Access Denied" page will display from TracCloud. If you would prefer to override this with a different page, enter that URL here.<br><br> | |||
* <b>Block SSO users from kiosk</b> | |||
::If enabled, anyone who logs in via SSO will not be allowed to open student-facing kiosks. This should only be enabled if your single sign-on service doesn't support single logout, otherwise if a user opens a kiosk, their campus account will still be logged in. | |||
</div> | |||
<hr> | |||
[[Category:TracCloud]] | |||
</div> | |||
Latest revision as of 15:29, 22 November 2024
TracCloud Technical Documentation
TracCloud Single Sign-on Configuration
TracCloud supports SAML, CAS, and LDAP for user authentication. Information on each of these options is available below.
We can be reached at helpdesk@go-redrock.com
With Redrock Software's Assistance
SAML
To setup SAML authentication, the following steps will need to be completed. At least one of the attributes being sent must match the contents of the username field in your Trac System, typically the first part of the email address. We can also use ID number, full email address, or other unique identifiers, but handle/username is preferred. Single logout (SLO) must be enabled for security purposes.
1. Install our Metadata
2. Send us your Metadata
- Either a URL or an XML file.
3. Send us a test account
- This makes implementing SAML on your system significantly faster, but isn't required.
CAS
To setup CAS authentication:
1. Add Redrock as an authorized service
- Here is our URL: https://sso.trac.cloud/cas_return.php
2. Send us your CAS settings
- CAS Login URL
- CAS Validate URL
- CAS Logout URL
LDAP
To setup LDAP authentication:
1. Send us your LDAP settings
- Server Address
- Port Number
- Service account name (if applicable)
- Service account password (if applicable)
- Base DN
Multiple base DN searches can be performed if needed.
Without Redrock Software's Assistance
If you're comfortable applying changes here and already have the information above, you can put these settings in place with any SysAdmin account. If you're having any trouble with these settings, feel free to reach out to us at helpdesk@go-redrock.com or by submitting a helpdesk ticket. LDAP currently requires additional configuration not available to non-Redrock accounts, reach out to us directly if you plan on using LDAP.
Other > Other Options > Preferences > Login & Security Settings > SAML
1. Install our Metadata
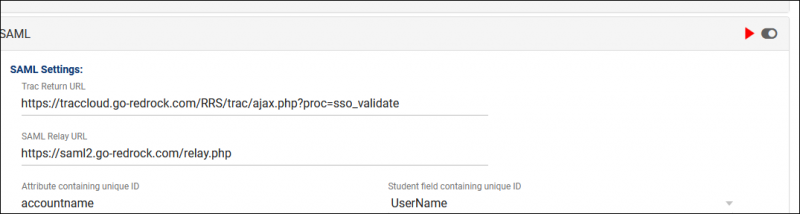
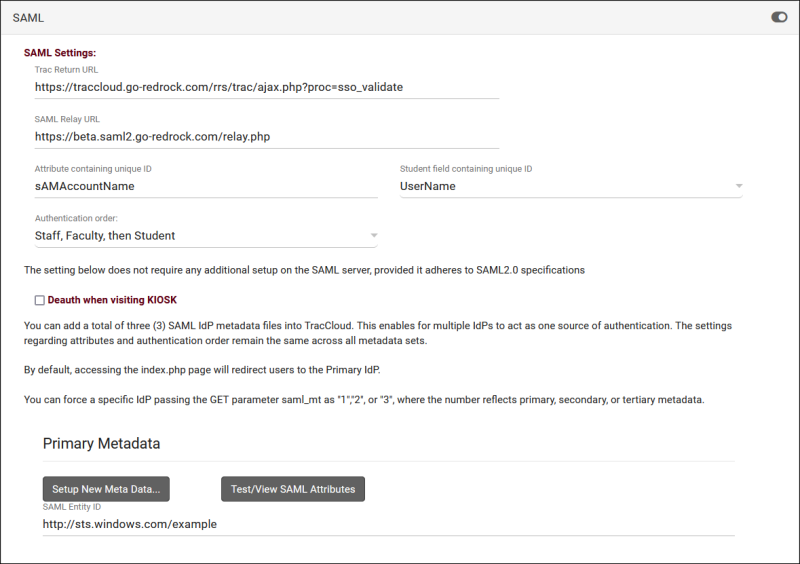
2. Fill out SAML settings
- Trac Return URL
- "https://traccloud.go-redrock.com/campuscode/trac/ajax.php?proc=sso_validate"
- Replace 'campus code' with your campus code, as seen in your URL. Otherwise static. Must be lowercase.
- If using a custom URL, use that in place of traccloud.go-redrock.com/campuscode
- SAML Relay URL
- "https://saml2.go-redrock.com/relay.php"
- This is static and never changes.
- Authentication Order
- Your staff may have more than one account type in the Trac System. You can use the "Authentication Order" preference to determine which account type authenticates first.
- Install your Metadata in the Primary Metadata field
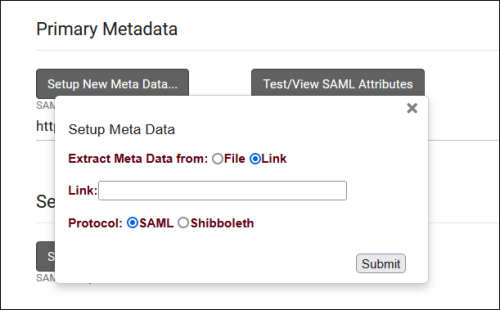
- After submitting, your Entity ID field will be populated automatically. If you require a duel-tenant configuration, reach out to us at helpdesk@go-redrock.com for assistance.
3. Retrieve your attributes
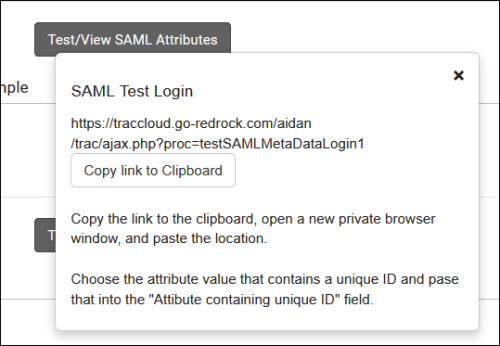
- Navigate to the provided URL in a Private/Incognito browser and login, you will be provided with a list of attributes and their value for the account that you used. Find the attribute that works for your system (e.g., first part of email address) and copy the name of that attribute into the "Attribute containing unique ID" field in TracCloud. This will need to correspond to the Username fields of accounts in the system.
4. Enable SAML
Other > Other Options > Preferences > Login & Security Settings > CAS
1. Add Redrock as an authorized service
- Here is our URL: https://sso.trac.cloud/cas_return.php
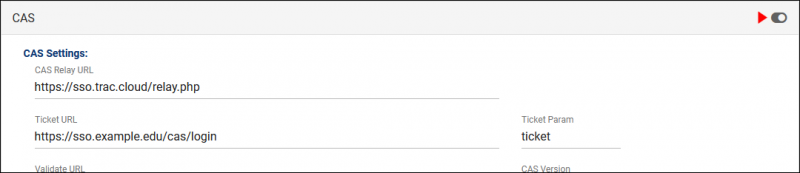
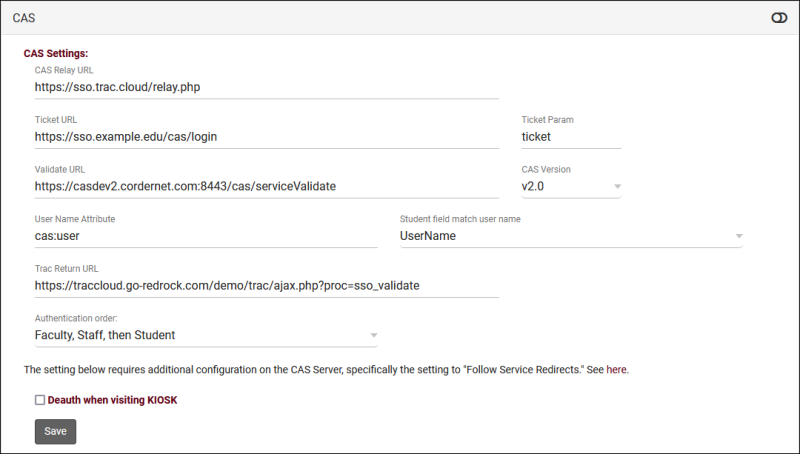
2. Fill out CAS settings
- CAS Relay URL
- "https://sso.trac.cloud/relay.php"
- This value is static and should not be changed.
- Ticket URL
- Place your CAS Login URL here.
- Ticket Param
- Typically "ticket"
- Validate URL
- Place your CAS Validate URL here.
- CAS Version
- Typically "2.0"
- User Name Attribute
- Typically "cas:user"
- Trac Return URL
- Place your CAS Logout URL here.
- Deauth when visiting KIOSK
- Kiosks are typically student-facing. If this is checked, it ends the SSO session to prevent a user from navigating to other campus services or even logging back into TracCloud.
3. Enable CAS
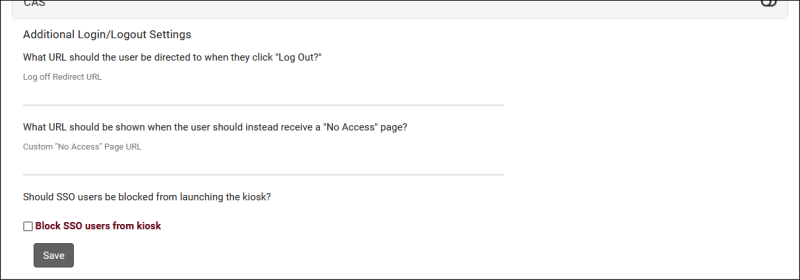
After setting up the SSO protocol, there are a few optional settings to configure, detailed below.
- Log Off Redirect URL
- This is the URL that users will be taken to when logging out of the Trac System, typically used to redirect users to a page that ends their single sign-on session.
- This is the URL that users will be taken to when logging out of the Trac System, typically used to redirect users to a page that ends their single sign-on session.
- Custom "No Access" Page URL
- By default, if a user attempts to access a page that they don't have access to, a generic "Access Denied" page will display from TracCloud. If you would prefer to override this with a different page, enter that URL here.
- By default, if a user attempts to access a page that they don't have access to, a generic "Access Denied" page will display from TracCloud. If you would prefer to override this with a different page, enter that URL here.
- Block SSO users from kiosk
- If enabled, anyone who logs in via SSO will not be allowed to open student-facing kiosks. This should only be enabled if your single sign-on service doesn't support single logout, otherwise if a user opens a kiosk, their campus account will still be logged in.